What is Phishing?

Small businesses in London can be exposed to cybercrime in a number of ways. Phishing scams are the most prominent techniques used by malicious actors.
Cybercriminals have been “Phishing” since the early days of email in the 1990s. Whilst phishing is one of the oldest techniques in the hacking textbook, multiple businesses in London fall victim to cyber-attacks.
Phishing is a form of cybercrime distinguished by its use of spoof emails, text messages or cold calls. Malicious actors essentially drop their bait and wait for someone to bite: hence the term “phishing” pronounced fishing.
The goal is to trick the target into believing they have received an email from a recognised company and asked to click on a link or download an attachment.
When a phishing link is clicked, it either infects the recipient’s computer with malware that can spy on user activity, install ransomware that takes over your IT infrastructure or directs you to a fake login page. If you were to key in your username and password, hackers have direct access to your real account.
According to reports, customers connected to at least 200 of the world’s leading brands are the victims of phishing attacks. The five most duplicated login pages are PayPal (11,000 pages), Microsoft (9500), Facebook (7500), eBay (3000), Amazon (1500).
A report on cybercrime published by the FBI in America, reveals that malicious actors stole $3.5 billion dollars from 114,702 victims in 2019. In the UK, the National Cyber Security Centre report shopping fraud costs Britain’s businesses £16.6 million during Lockdown 1 between March and June 2020.
How To Identify Phishing Scams
Phishing attacks are emails that assume the identity of a trusted source; a bank, company, employer, hospital etc. When taken at face value by unsuspecting victims, the email appears to be genuine.
However, there are key indicators that enable you to identify whether an email may be a phishing scam.
Random Business or Offer
Some phishing scams are easy to identify. They are sent by random companies purporting to provide “the best services” or reveal secret information etc.
These type of phishing scams are easy to spot, although they could actually be from a genuine company trying to drum up business through cold-calling. This is an illegal marketing practice so you should ignore these type of emails to be on the safe side anyway.
No Personalisation
The majority of businesses you register with today will only send you personalised emails. Cybercriminals sending out spoof emails are mostly sending random emails to millions of people.
If you receive an email that is not addressed to you personally but appears to come from a company you are a customer of, treat the email as fraudulent. The email will typically start off with “Dear Customer”.
Sense of Urgency
Sophisticated techniques replicate emails you would expect to receive from a trusted third-party as mentioned above. The messages typically urge recipients to take immediate action and click a link or open a document.
The type of messages you should be checked carefully include:
- Notification of suspicious activity on your account. The details will explain there has been a log-in account from a device in a certain location and you should click a link to report the matter if it was not you.
- Messages from a company asking for you to confirm personal information
- Fake invoices that make you think someone is using your credit card
- Links claiming to give you access to your account or confirm a purchase
- A false claim there is something wrong with your account and prompting you to click a link
- Notification of a backup file on your website with a link to access backup details
- Claim you’ve won a prize
- Confirm you are eligible for a government grant or tax refund
- Offer free merchandise with a special coupon
Fake email address
It should be noted that cybercriminals that use more sophisticated techniques pretending to be a particular company send out millions of emails to random people in the hope some of them will be affiliated with the company they are pretending to be.
For example, you may receive an email from Amazon saying there is a problem with your account, but you are not an Amazon customer.
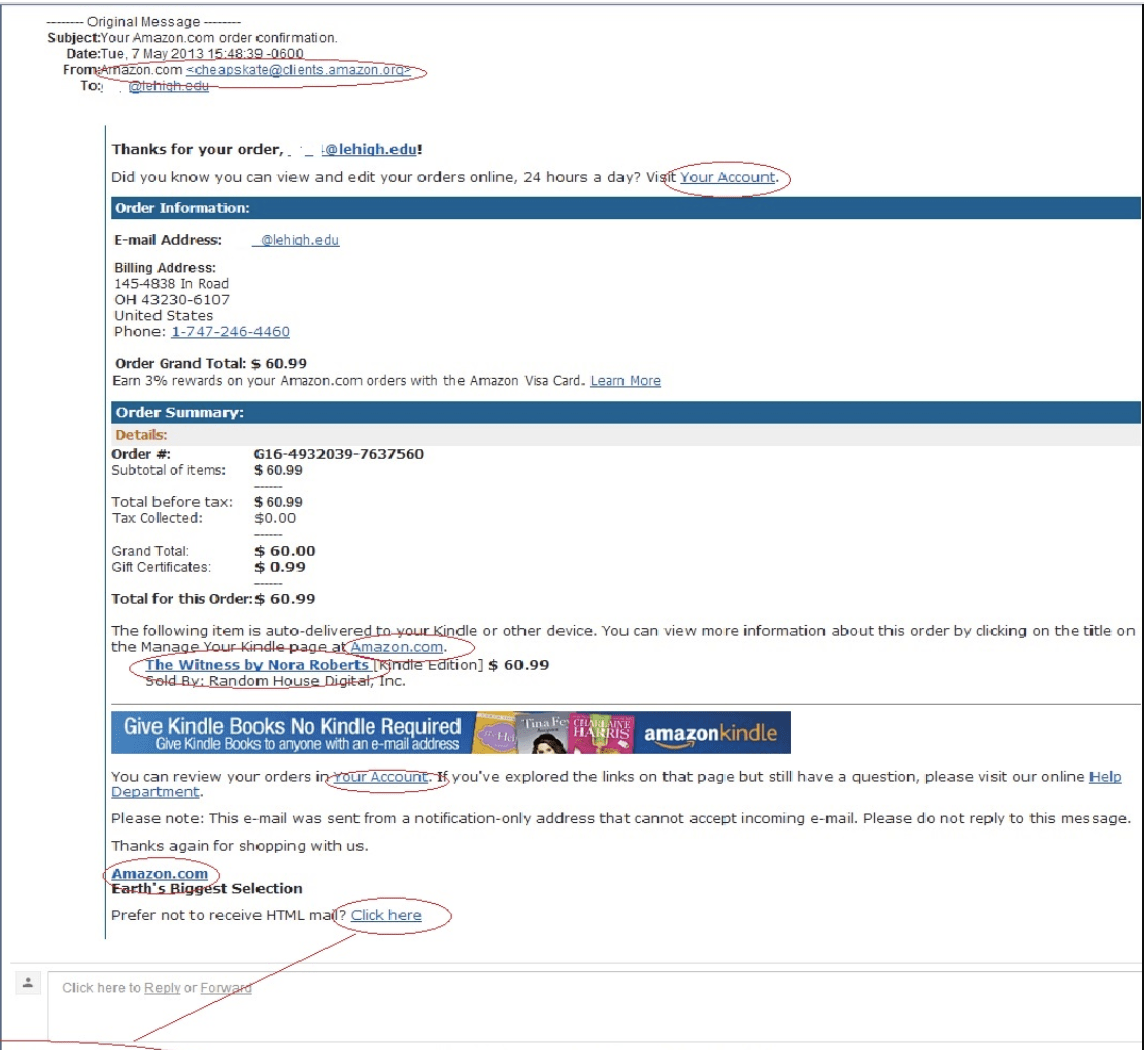
But what if you are an Amazon customer? Unless you’re aware of phishing scams, you can easily be lured to click on the link in the email to investigate the matter.
For all intents and purposes, the email will look genuine. It will include the Amazon logo and appear like an official receipt. However, there are telltale signs.
Ordinarily, the email address will look suspicious. In the example below, you can easily see the email is not genuine: cheapskates@clients.amazon.com.
Regardless of the “cheapskates” part, fake emails from companies will almost always have an anomaly in the latter part of the sender address such as __________@accounts.Amazon.com.
A genuine email from a company usually has an appendage stating the company name only, i.e. __________@Amazon.com.
Before you click on any links or download documents sent to you by companies you are a customer with, always check the email address looks genuine.
Infected files
Some types of phishing emails will attempt to encourage the recipient to open a file infected with malware or access a folder stored in the cloud.
These types of phishing scams target end-users that typically would ordinarily have contact with third-parties such as someone in HR receiving a CV from a prospective employee.
Freelances that use third-party websites are also susceptible to phishing attacks. You may be offered what you think is a good job opportunity and sent a document that is infected with malware.
Typical techniques usually involved attachments which are .zip files or cloud service which with a suspicious url: googledocs/buyingguides/bit.ly.
Unless you receive a document from a trusted source, do not open any documents without installing anti-malware software on your computer.
Social Media Spyware
Earlier this year, Facebook filed a lawsuit against two companies, Oink and Stuff, that used social media extensions to scrape user profile data and browser-related information.
According to Facebook, the extensions downloaded by their users “were malicious and contained hidden computer code that functioned like spyware.”
Malicious Browser Extensions
Recent reports described how more than three million people have been tricked into installing extensions for Chrome and Edge which redirect users to a third-party website.
Research conducted by Avast found the malicious code redirects users to targeted ads and phishing sites. For every redirect, the hijackers receive a monetary reward.
Other extensions are programmed with code that can access browsing data or collect personal data that is active on the infected device.
What is Spear Phishing?
Spear phishing differs from general phishing scams in that they seek to target specific individuals; heads or members of organisations and business owners are common targets.
The goal is to either install malicious malware on the targets computer or prompt them to divulge sensitive information. Messages are modified to specifically address the target and will appear to be from an entity they are associated with.
It’s plausible that cybercriminals acquire relevant information to pursue spear-phishing scams from companies that sell data to third-parties. However, it is also possible to acquire this information from social media accounts and websites.
A common theme is for cybercriminals to target website owners of businesses through the contact form or an email promoted on your website.
What is Whale Phishing?
As the term implies, Whale Phishing targets ‘big phish’ – high-value targets that are wealthy or can be held to ransom. C-suite executives, celebrities, politicians, and other prominent figures in the community are the targets of whale phishing.
How To Combat Phishing
Well-orchestrated phishing emails can be difficult to detect to the untrained eye. The Department for Digital, Culture, Media & Sport reports 80% of UK businesses that suffered a data breach were victims of phishing emails.
It is, therefore, important to raise awareness of cybercrime and install preventative measures that eliminate data breaches, or at the very least mitigate the damage.
- Stay up to date with the latest phishing techniques
- Analyse emails for authenticity before you click on links or downloads
- Verify a website is legitimate, professional and secure (does it have the https security lock?)
- Make a habit of regularly updating the passwords to any online accounts that stores sensitive data
- Install a reputable anti-phishing tool on your browser that detects websites listed as a known phishing site
- Avoid clicking anything on pop-up windows on suspicious websites. If you are directed to another site via a pop-up, it is almost guaranteed to pose a security threat
- Keep browsers and operating systems secure by running software updates – they often have a security patch covering a vulnerability in the current edition
- Install high-grade firewalls in addition to the firewalls that come with your device as standard
- Never volunteer personal information. If you do need to contact a company you are a customer with, navigate to their website via your web browser or call them using the number provided on their website
- Install anti-software
- Adopt the services of IT Support professionals that use advanced technologies to detect suspicious behaviour, apply security patches and safeguard your business network
IT Support Cybersecurity Services in London
To avoid your customers becoming a victim of phishing attacks, businesses have a responsibility to reduce the risk, provide useful information, staff training and install anti-virus software that effectively protects your network.
When you make it difficult for attackers to reach your customers and your employees, phishing emails are more difficult to appear authentic.
The National Cyber Security Centre recommend protection and prevention strategies should be addressed in five layers:

Layer 1: Tools and Training
Use Anti-spoof email addresses. Contact customers using a different email address than the one that is publicly available on your website or letterheads. You can do this by creating email addresses with anti-spoofing controls such as DMARC, SPF and DKIM.
Educate your customers about leaving a digital footprint. Recommend they use secure passwords that are not linked to family members, pet names, birthdays, favourite books/films or any other personal information they may typically share on social media networks.
Train your employees. Identify how sharing sensitive data about themselves or your organisation across social platforms can be used in phishing emails. Personnel that correspond with partners, suppliers, contractors or other third-parties should be extra vigilant when providing payment details.
Use email filters. Standard email filters can identify suspicious email addresses that are associated with cybercrime. IT support services use an email client with built-in spam filters or can create a bespoke service for your email server to detect suspected phishing email and block certain IP addresses, domain names and blacklisted email addresses.
Install anti-virus software. Cybersecurity tools scan a computer system and can detect all types of malicious code associated with spyware, adware, trojans and worms.
Layer 2: Identify and Report Suspected Phishing Emails
Train employees to spot phishing emails. Cybersecurity companies report that more than 99% of data breaches are due to human error. Phishing attacks could easily be prevented if your employees and customers know which signs to look for.
Encourage staff to report phishing emails. The cybersecurity policy for every business should document a protocol for staff members to follow if they suspect a phishing attack. Sometimes, a suspected case may actually be a legitimate email so don’t reprimand staff that are not able to differentiate between scams and authentic emails. If your staff fear reprisals, they may fail to report an actual attack.
Revisit training and reporting protocols. Techniques used by cybercriminals are becoming more sophisticated. Off-the-shelf tools can be used to design emails that appear to be authentic. Personnel in departments that are most likely to receive unsolicited emails from outside the organisation should be given regular training. Although employees on the frontline may not be of much interest to malicious actors, they can be used as a stepping stone to infiltrate your business networks with malicious malware or gather information that can be used for a spear-phishing campaign; i.e. can you put me in touch with someone that works in your accounts department.
Install two-way verification. Operational processes such as logging into accounts and making payments can be tightened by using a second type of communication to verify users such as an SMS or phone call.
Invest in cloud computing. Sharing files via cloud platforms avoid employees from being tempted to open attachments sent via email. If you are working with contractors from outside the company, cloud software access limits can be given to third-parties. This ensures that little to no damage can be caused to your system in the event hackers discover the username and password of the third-party freelancer.
Layer 3: Minimise damage caused by undetected phishing
Protect all devices from malware. Employees are using multiple devices to access work emails and company data – including personal devices. Cybersecurity best practices involve installing advanced anti-malware tools on every device that is or may be used for work purposes. IT support professionals specialising in network security recommend configuring devices with encrypted code and using endpoint defences that prevent malware from being installed.
Insist on supported devices. To reduce the risk of cybercrime, you have the option to ban employees from accessing data or accounts stored on the company’s network via a personal device. This can be quite difficult in the age of remote working. The only option is to supply employees with a mobile device they are only permitted to use for work purposes.
Limit account access/payment levels. IT software enables users to be given specified privileges that enable them to perform certain tasks. Limit the number of people that have access to critical data to management or trusted members of staff that are responsible for performing specific roles as part of their job; i.e a junior in accounts may only be authorised to make payments <£5000, a senior member has an authorisation up to £25,000 and a senior manager or C-level executive has unlimited access.
Run a proxy server. This detects websites that host malware or phishing campaigns. The National Cyber Security Centre also provides internet users with a free and reliable protective DNS (PDNS) which prevents access to domains that are known to be malicious.
Layer 4: Responding to Incidents
Report Incidents. Phishing attacks are inevitable. Employees should have a procedure in which they are encouraged to report suspicious emails, texts and phone calls. It’s also important that they are not made to feel guilty or reprimanded if their device is compromised otherwise staff will be discouraged from reporting incidents.
Install monitoring software. Security logging systems identify suspicious behaviour when someone is trying to log in to an account or in the actual system such as the transfer or deletion of bulk files. With an advanced cloud security monitoring service your IT infrastructure is covered 24/7.
Wrap Up
Phishing and other forms of cybercrime are a threat to your business. What’s more, companies face potentially crippling fines under the General Data Protection Regulations (GDPR).
Don’t run the risk of your IT infrastructure being compromised. MicroPro offers advanced cybersecurity services and a wide range of managed IT solutions and IT Support in London that ensure your company’s entire IT infrastructure is secure and running smoothly.


