Can Your Staff Spot Phishing Scams and Other Cyber Attacks?

Phishing scams are a common method used by cybercriminals to reap ill-gotten gains. According to statistics, hackers cost the global economy around $6 trillion in 2022.
This figure is expected to rise to $10.5 trillion by 2025.
Identifying and avoiding phishing attempts is crucial for safeguarding the data of your business, employees and customers. Falling victim to a phishing scam can lead to financial losses for individuals and can put companies out of business.
Scammers can use stolen information to commit fraud, make unauthorised transactions, or gain access to bank accounts. By recognising fraudulent phishing attempts, employees can help protect the financial interests of your customers, your company and themselves.
Business owners of all sizes should be taking cybercrime more seriously. Last year, the UK’s Information Commissioner’s Office issued a warning saying that the biggest threats to business continuity is not hackers, it’s complacency.
“The biggest cyber risk businesses face is not from hackers outside of their company, but from complacency within their company. If your business doesn’t regularly monitor for suspicious activity in its systems and fails to act on warnings, or doesn’t update software and fails to provide training to staff, you can expect a similar fine from my office.” ~ John Edwards, UK Information Commissioner
Companies that take cybersecurity seriously and actively educate their employees about phishing and other cyber threats. Taking a Zero-Trust approach can instil trust in your customers. When customers see that an organisation is proactive in protecting their data, they are more likely to continue doing business with them.
Are Phishing Attacks Common?
Phishing is the leading strategy hackers use to trip businesses up. According to the latest industry statistics (September 2023), an estimated 3.4 billion spam emails are sent every day.
Security firms also tell us that 91% of cyber attacks begin with a phishing email and 79% of successful data breaches in the UK originated with a phishing email.

What are Phishing Scams?
Phishing scams are deceptive attempts to trick individuals into revealing sensitive information, such as login credentials, personal identification, financial details, or passwords.
These types of hacking scams typically involve the use of deceptive emails, websites, or messages that appear to be from reputable sources such as banks, social media platforms, government agencies, or well-known businesses.
The most successful phishing scams come from trusted sources such as a partner you do business with, a supplier, or a high-ranking official within a company — usually someone with the authority to authorise the transfer of funds.
Check out this list of the 12 most costly phishing scams and you will notice a significant pattern — trust!
How Phishing Scams Work?
Phishing emails have specific characteristics to look out for. Hackers use various tactics to lure victims across various platforms; phishing emails, smishing SMS and voice calls (vishing).
Phishing attempts typically claim there’s a security issue with your account and you need to login or verify your information, an important action is required and you need to fill out a form, an invoice needs paying or your need to reset your login details for security reasons.
Here’s an example:
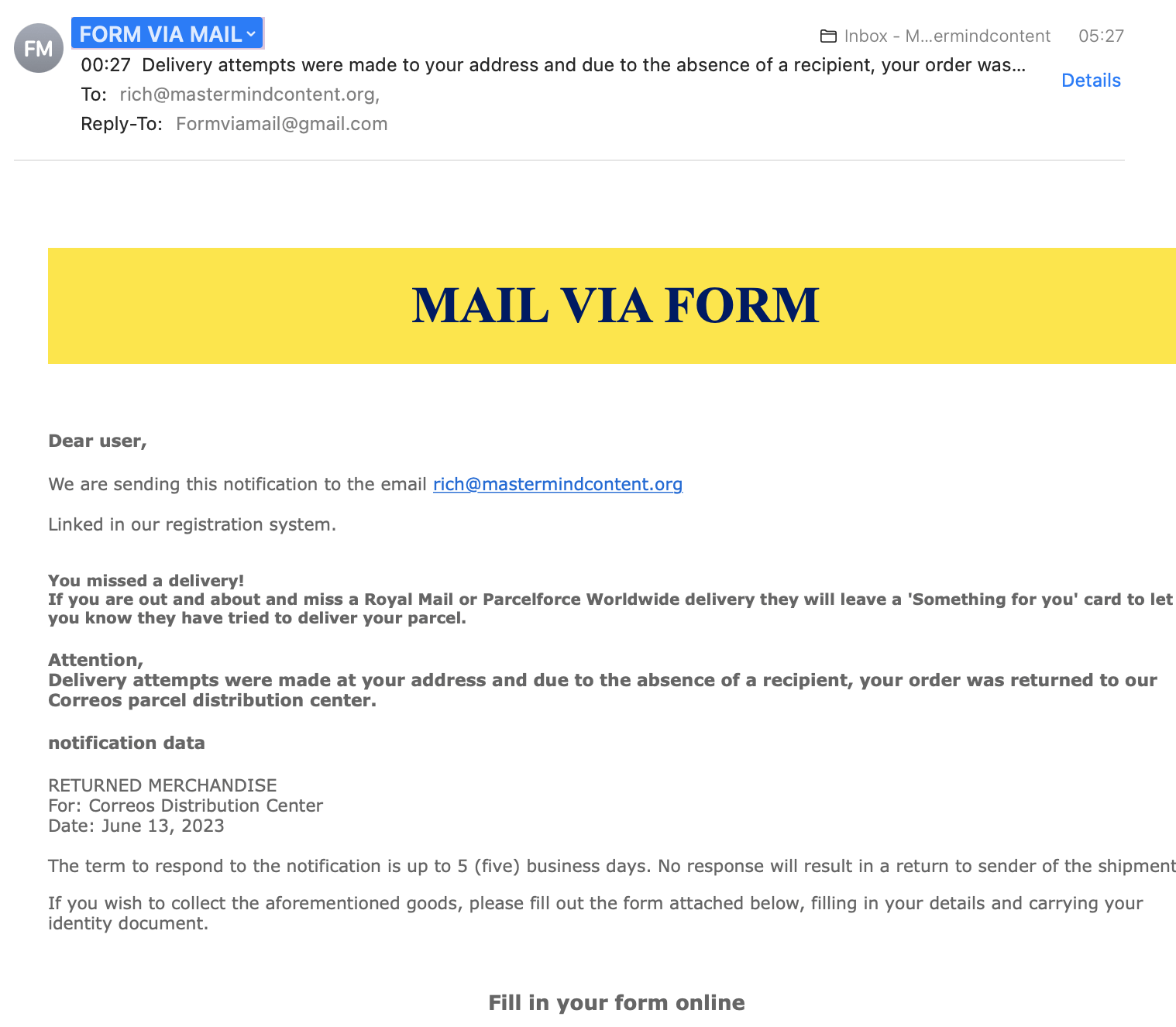
Hackers use various means of soliciting information they can use to their benefit. Listed below are the most common strategies to look out for. If you are unaware of how hackers attempt to trick victims, it’s easy to see how a member of your staff can slip up.
What Are Common Techniques Used in Phishing Scams?
Phishing scams are becoming increasingly sophisticated and can take various forms. This can make social engineering difficult to detect if your staff is not aware of where and how threats can arise.
It’s important to be cautious when dealing with any outside contact. Cybersecurity best practices should adopt a no-trust policy which involves verifying the authenticity of any request for personal information or financial details.
Always double-check the sender’s identity, scrutinise messages for red flags, and be wary of unsolicited communication requesting sensitive data. If in doubt, contact the organisation directly through official channels to confirm the request is legitimate.
Links to Fake Websites
Phishing emails frequently contain links that direct recipients to counterfeit websites designed to mimic the appearance of a genuine brand login page. These fake sites are set up to capture sensitive information when victims enter their credentials.
If you’re a patron of the company hackers are purporting to be, you can quite easily enter your login details and hand your account straight over to hackers.
Malicious Attachments
Phishing emails may contain malicious attachments (e.g., PDFs or Word documents) that, when opened, infect your computer with malware.
Hackers also drop malicious attachments into chat streams such as the incidents discovered last year when malware was being dropped into Microsoft Teams. Again, there is the issue of trust here. Staff members will readily open documents that appear to come from colleagues through an app they assume is secure.
And we all know what assume does!
Social Engineering
Cybercriminals often employ psychological manipulation techniques to make their messages more convincing. Urgency, fear, curiosity, or empathy are all ways hackers tug on our emotional strings to trick individuals into taking actions that benefit the attacker.
Spear Phishing
In spear phishing attacks, scammers tailor their messages to specific individuals within a company — typically with staff members who have access to accounts or who can authorise payments; CEOs, accounts managers, account clerks etc.
Spear phishing attacks or whaling involves gathering relevant information from social media or other sources to increase their credibility. Data that has been stolen from infected computers using spyware can also be used to create phishing emails that appear plausible.
Credential Theft
The primary goal of many phishing scams is to steal login credentials (e.g., usernames and passwords) for online accounts, which can then be used for identity theft or unauthorised access.
Attackers create realistic-looking login pages, often via email or websites, to trick targeted victims into entering credentials.
Financial Fraud
Phishers may use stolen information to commit financial fraud, such as making unauthorised purchases, withdrawing funds, or accessing bank accounts.
Identity Theft
With access to personal information, attackers can engage in identity theft, opening fraudulent accounts or committing other crimes in the victim’s name.
To protect yourself from phishing scams, it’s essential to remain vigilant and follow best practices, such as verifying the legitimacy of communication, not clicking on suspicious links or downloading attachments from unknown sources, and regularly updating your passwords.
Fake Social Media Profiles
Attackers can create fake social media profiles, often impersonating someone you know, to send you malicious links or requests for personal information.
Smishing (SMS Phishing)
Phishers send text messages with links or phone numbers to call, claiming you’ve won a prize or that there’s a problem with your account.
Vishing (Voice Phishing)
Scammers call you, pretending to be from a reputable organisation and requesting sensitive information like credit card details or SSNs.
Fake Surveys and Contests
You receive emails or messages promising rewards for participating in surveys or contests but require personal information to claim your prize.
Tech Support Scams
Sophisticated hackers might impersonate tech support members by phone or email claiming you have a virus on your computer or asking you to update your login details for security reasons. Some scams may ask for remote access to your computer.
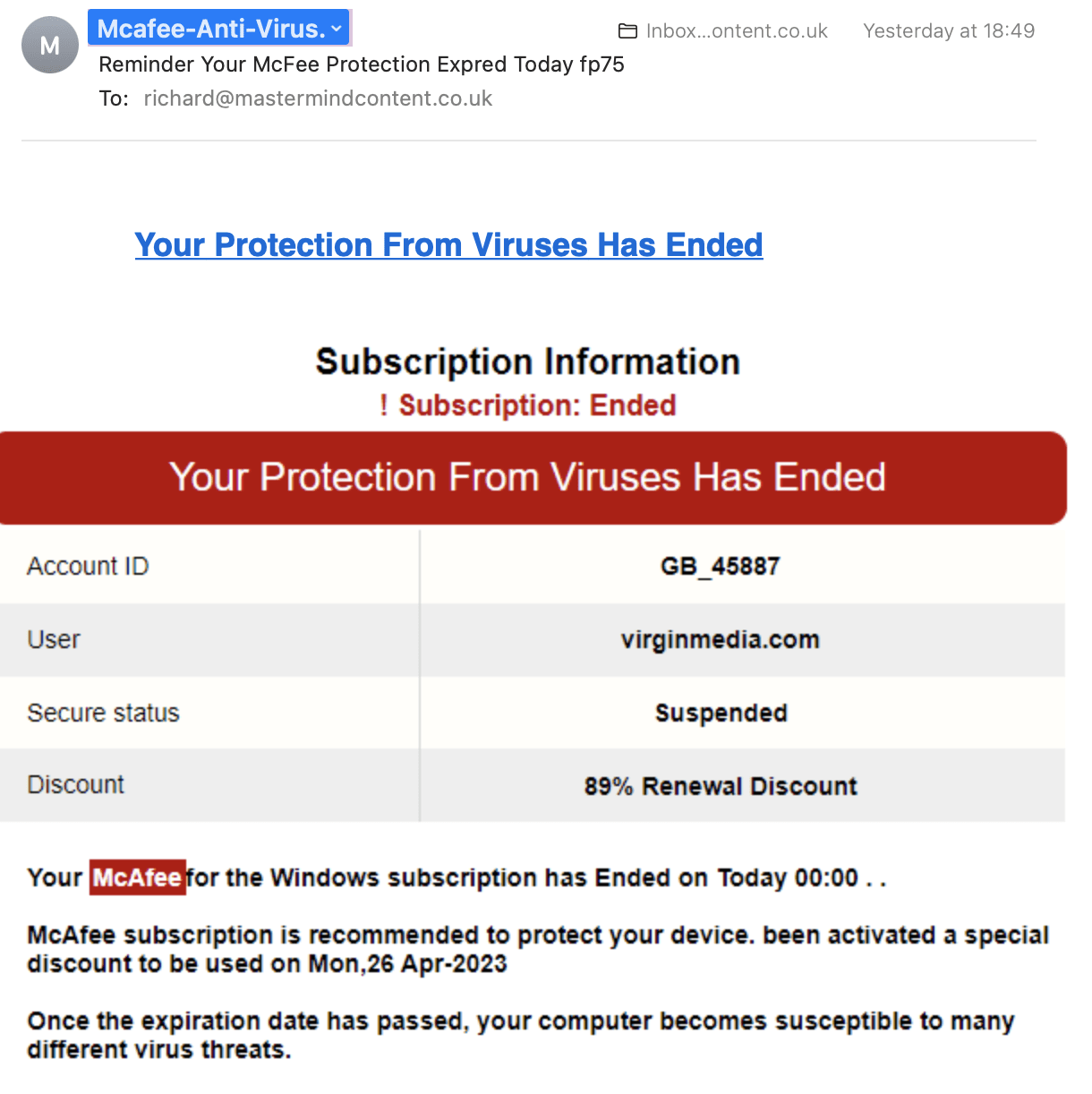
How can you Identify Phishing Scams?
Phishing scams often choose specific targets, whether individuals or organisations, based on factors like perceived vulnerability, the potential value of stolen information, or specific objectives (e.g., gaining access to corporate networks).
Whilst many amateur hackers fail to convince, like the example below, sophisticated hackers can make their phishing attempts pretty convincing. And now bad actors are using FraudGPT, you should expect the standard of convincing phishing scams to go up a notch or three.
There are some red flags that continue to stand out down the years, We’ve listed them below:
Generic Greetings
Be suspicious of emails or SMS messages that use generic greetings like “Dear Customer” or “User.” Legitimate businesses usually address you by name in their communications.
Unexpected Emails
If you receive an unsolicited email or message asking you to click on a link, download an attachment, or provide personal information, be cautious. Verify the sender’s identity.
Urgent or Threatening Language
Nefarious actors often use scare tactics to pressure you into taking immediate action. They may claim your account is in danger or that you’ll face consequences if you don’t act quickly.
Suspicious Links
Hover your mouse cursor over links in emails to see where they lead. Be cautious of links that don’t match the official website’s domain or use misspelt URLs.
Misspellings and Poor Grammar
Phishing emails composed by non-English speakers often contain spelling mistakes, grammatical errors, or awkward use of the language.
Spoofed Sender Addresses
Spoof emails are often the most difficult to detect These types of scams can accurately mimic brand emails. The only way to identify the emails are fraudulent is by the email address.
The sender’s email has to be manipulated to appear as if it’s from a legitimate organisation, but there is usually an anomaly of some description. Double-check the sender’s email address for inconsistencies.
You can also hover your cursor over the email so that the actual address appears rather than the published email address. Spoof emails do not always match the visible address.
Requests for Personal Information
Legitimate organisations rarely ask for sensitive information like passwords, credit card numbers, or Social Security numbers via email or chat.
Check the URL
Before entering login credentials or financial information on a website, ensure the website’s URL starts with “https://” and has a padlock icon in the address bar, indicating a secure connection.
Verify Requests
If you receive a request for sensitive information, contact the sender directly through official channels to verify the request’s legitimacy.
Be Wary of Pop-ups
Avoid clicking on pop-up windows or ads that request personal information.
What is a Zero-Trust Policy?
The best way to prevent a data breach of any kind is to implement a zero-trust policy. Often referred to as Zero Trust Security or Zero Trust Network, these protocols are designed to install a companywide cybersecurity framework that challenges the traditional notion of trust within a chain of command.
Instead of assuming trust based on individuals (inside or outside the corporate network), a zero-trust approach assumes that no entity, regardless of status, should be trusted by default.

The strategy is built on continuous verification of the identity and security posture of every user, device, or application trying to access resources. Key principles and components of a zero-trust policy include:
Verify Identity
Users and devices must authenticate and prove their identity before gaining access to resources. This authentication often involves multi-factor authentication (MFA) for added security.
Least Privilege Access
Users and devices are granted the minimum level of access required to perform their tasks. This principle reduces the potential damage caused by a compromised account.
Micro-Segmentation
Networks are divided into small, isolated segments, limiting lateral movement for attackers within the network. Access between segments is controlled and monitored rigorously.
Continuous Monitoring
Continuous monitoring and assessment of user and device behaviour help detect anomalies or suspicious activities. Any unusual behaviour triggers alerts and may result in access revocation.
Strict Access Control Policies
Access control policies are strictly enforced, with access decisions based on a combination of factors, including user identity, device security posture, and contextual information.
Encryption
Data in transit and at rest is encrypted to protect it from interception and unauthorised access.
Network Micro-Segmentation
Network segmentation is used to isolate different parts of the network, and access between segments is restricted based on the principle of least privilege.
Application-Centric Security
Rather than focusing solely on the network perimeter, Zero Trust places an emphasis on securing applications and data, regardless of their location (on-premises, cloud, or hybrid).
Continuous Access Reevaluation
Access permissions are not static; they are continually reevaluated based on changing circumstances, user behaviour, and security postures.
IT Support in London
As an experienced managed IT Support Provider in London, Micro Pro recognises that traditional perimeter-based security is no longer sufficient in today’s complex and dynamic IT environments.
To protect your business from suffering a data breach we design a zero-trust policy to protect your employees and customers against insider threats, external cyberattacks, and lateral movement by attackers who have already breached the network.
Moreover, we implement comprehensive cybersecurity training programs to educate employees about the risks associated with phishing scams and how to recognise and report attempted cybercrime in its various forms.
Our cybersecurity awareness training typically covers best practices for identifying phishing emails, suspicious links, and social engineering tactics. It also emphasises the importance of reporting potential threats to your IT or security team promptly.


