What is FraudGPT And What You Can Do About It

ChatGPT vs FraudGPT
You’ve probably heard of ChatGPT right? But have you heard of its evil twin FraudGPT?
If not, listen up. Petty cybercriminals have access to a tool which is a game-changer for them. But don’t panic, if you’re vigilant, you should still be able to fend off little boys phishing in a big pond.
First off, what is fraudGPT?
“FraudGPT” is a nefarious tool that is being sold to hackers for $200 a month on the dark web and Telegram. Like ChatGPT, FraudGPT uses an AI-powered Generative Pre-trained Transformer model that has the capability to iterate various natural language tasks.
So why is a FraudGPT a game changer for small-time cyber criminals?
Let’s Talk About Hacks Baby
We know that cybercrime exists and that it potentially poses significant problems to the business continuity of regular companies. We also know how most hackers conduct their strategies.
And that’s really the good news in all of this. Cybersecurity specialists and anti-malware makers are able to prevent over 90% of attacks. Especially attacks on regular companies that are being targeted by small-time threat actors that are using malware that is known to various cybersecurity agencies and can be captured.
Most of the media-reported data breaches involve multi-million dollar companies. More often than not, the reports also reveal that said company is believed to have been attacked by a ‘state-sponsored’ cybercriminal network.
Needless to say, state-sponsored networks have a glut of crack hackers at their disposal. The same can be said for major corporations that pay their ‘ethical hackers’ handsomely.
So that leads us to the petty threat actors that mostly target regular businesses. You probably know from experience that they’re not very good. As a matter of fact, some of their phishing attempts are so bad, my 83-year-old mother would realise something there is something phishy about this email.
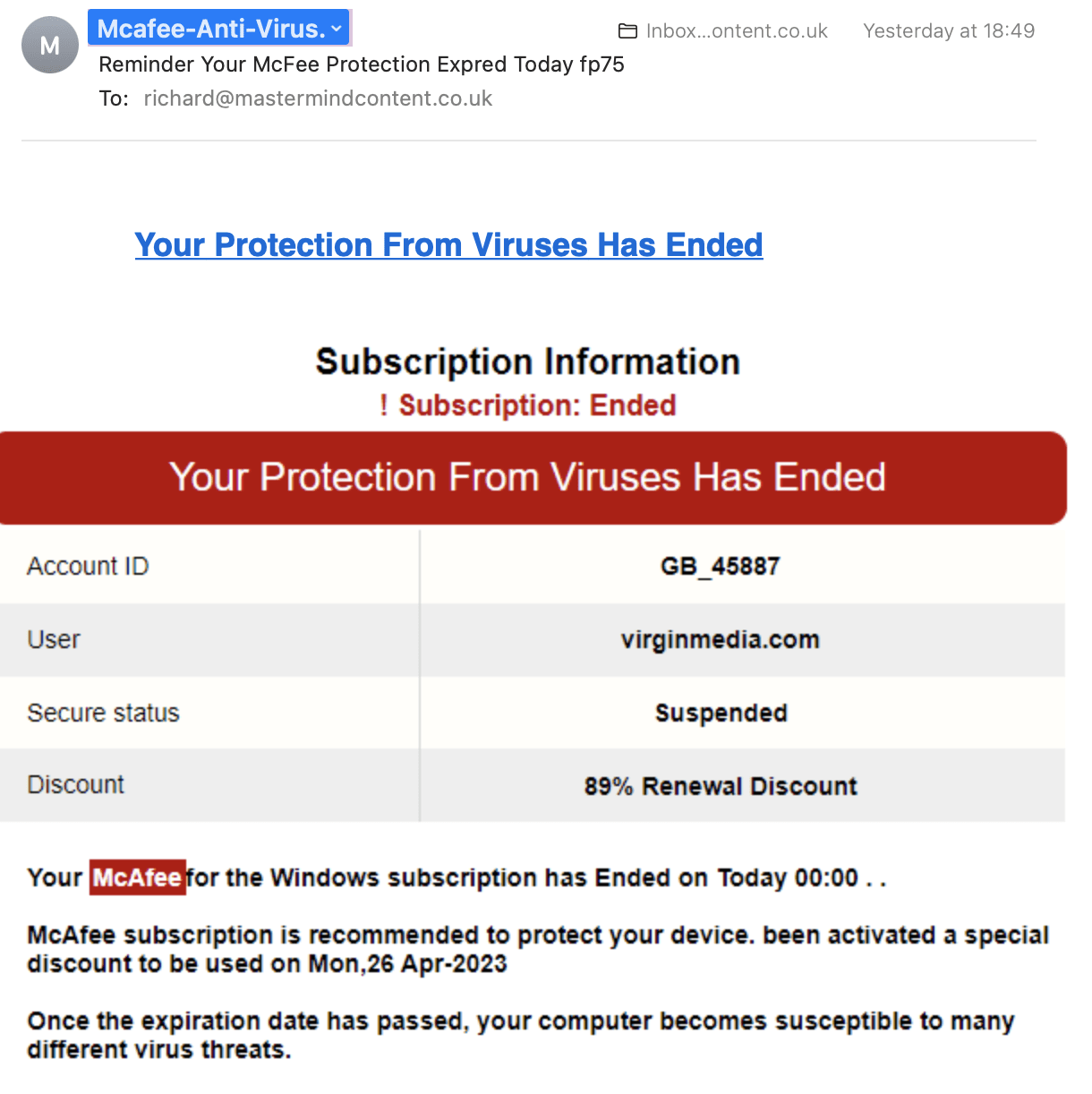
It’s clear to see this phishing attempt has not come from McAfee.
Here’s the thing. Most small-time criminals rely on employees to make a mistake by clicking on infected links or downloading a document. But as you can tell by the wording in the above example (which is common), nobody is going to fall for poorly constructed emails.
The majority of small-time hackers live in non-English speaking countries. They make simple spelling and grammar mistakes and don’t know how to write a formal business approach.
It was because of this inefficiency that it was ordinarily easy to identify phishing attempts.
FraudGPT removes that red flag by enabling amateurish threat actors to create official-sounding emails that could more readily fool unsuspecting employees.
What are the consequences of a data breach?
Online fraud is a significant concern for UK businesses across various industries. Detecting and preventing cybercrime can be the difference between business continuity and bankruptcy.
Reports reveal that 60% of businesses fail within six months of a data breach. You might think the companies go out of business because of the money that is stolen from them. ]
However, most businesses collapse because they can’t generate enough cash flow to recover from a data breach. That’s because GDPR forces businesses to declare they have suffered a data breach.
Declaring a data breach results in hefty legal fees and reputational damage. Reports indicate that 72% of shoppers do not return to brands following a data breach. They do not trust them to keep their data safe.
It goes without saying that firms should have a thorough understanding of the types of fraud risks they face within their industry and operations.
Whilst automated fraud detection systems powered by AI and NLP technologies can detect fraud in real-time or near-real-time, a specialised tool like FraudGPT could give hackers ammunition that enables them to fraudulently extract money or information from companies without them needing malware.
It’s clear that GDPR does not work for regular businesses. The question is whether standard cybersecurity practices will as well.
FraudGPT could make the entire digital cybersecurity industry redundant.
But there are other ways to defend your business from threat actors.
Combatting FraudGPT
The general advice stemming from IT security specialists is to implement robust fraud prevention measures, including strong authentication protocols, encryption, and access controls. Regularly update and patch software and systems to minimise vulnerabilities.
Some firms also suggest considering using AI and NLP technologies for fraud detection. Machine learning models can analyse large datasets to identify patterns and anomalies associated with fraudulent activities.
But whilst such models can be trained to recognise suspicious language or behaviour in text data, emails and online forms etc, FraudGPT eradicates these standard industry practices.
It’s clear that businesses have to focus their cybersecurity efforts on raising employee awareness. It’s well known that around 90% of data breaches are due to human error. Eliminate that huge slice of danger and you dramatically reduce the risk of a data breach.

We’ve written extensively about the necessity to train your staff in cyber awareness. For more tips and tricks, read our article, “Cybersecurity Solutions Don’t Have To Be Expensive.”
Cybersecurity solutions that work best detect and prevent cyberattacks, data breaches, and other online threats. So it’s in your best interest to understand what the latest hacking strategies are. Otherwise, you can’t detect them.
Here are some cybersecurity solutions.
Get Educated About Current Cybersecurity Threats
Cybersecurity is an ongoing process as threat actors constantly evolve their strategies — and technologies. Therefore, it’s crucial to maintain a proactive and vigilant approach to cybersecurity by staying informed about the latest threats and taking appropriate measures to protect your organisation’s digital assets.
From time to time, Micro Pro publish articles detailing the latest hacking techniques. We will continue to do so.
It’s also a good IT that your cybersecurity task force conducts its own research as well. There are plenty of reputable cybersecurity news websites and blogs that provide up-to-date information on the latest threats, vulnerabilities, and trends.
Large companies may want to consider subscribing to security industry reports and publications that publish the latest news coming from leading cybercrime companies like Symantec, McAfee, and Cisco. Cybersecurity firms also promote threat intelligence feeds and own social media accounts.
Other worthwhile sources to sign up to are cybersecurity alerts and resources provided by government agencies, industry-specific ISACs or Information Sharing and Analysis Organisations (ISAOs). These groups facilitate the sharing of threat intelligence within the same sector.
Integrating threat intelligence feeds and APIs into your security infrastructure to automate threat detection and response is also becoming a common practice.
Companies that don’t have the staff resources of IT security expertise should be looking to team up with outsourced IT support specialists in London that do have the resources and expertise.
Employee FraudGPT Training
We’ve been saying this for years, but we’ll continue to say it: training employees on how to recognise and report potential fraud should be a priority.
You can read how to prepare and perform cybersecurity training for your staff in this article. However, it’s clear that training practices will need updating as cybercrime strategies evolve.
Such as FraudGPT.
This is why the first step to protecting your company data has to start with an understanding of the latest cybercrime strategies. Your employees should be informed, trained and tested.
If you haven’t already, create a comprehensive cybersecurity policy that outlines the rules, best practices, and expectations regarding cybersecurity. Ensure that all employees have access to this policy. Focus on the topics most relevant to your industry and the roles of employees across each department.
For example, employees that have access to funds and other sensitive data will require additional training. As we discussed in our article, Are Hackers Targeting Your C-Suite With Whaling Attacks, executives and account managers can easily be duped into transferring funds by clever hackers.
And whaling attacks are the reason why FraudGPT is such a dangerous and powerful weapon for threat actors. Awareness of standard phishing attacks is not enough anymore.
It’s easy to see that FraudGPT can and will make social engineering attacks more prominent and effective. To help raise awareness and attentiveness, instil best practices into your employees by conducting simulated phishing attacks to test their ability to recognise phishing attempts and deal with them accordingly.
Now that FraudGPT-generated phishing attempts advanced the capabilities of hackers to deceive targets, the only way to identify whether an email is a security threat is to check the email address and confirm the sender is legitimate.
You can also periodically reinforce cybersecurity awareness through reminders, quizzes, and follow-up training sessions to keep the potential for threats fresh in the minds of your employees. Use positive reinforcement for good security practices and create a cybercrime reporting culture.
But most importantly, companies need to promote a security-first mindset and establish a zero-trust policy. Encourage employees to think about security in their daily tasks. Teach them to be cautious, verify information, and verify requests for sensitive data.
Also, ensure that senior leadership actively supports and participates in cybersecurity awareness initiatives. This sends a clear message about the importance of security. You may also want to acknowledge and reward employees who demonstrate exemplary cybersecurity practices or who report security incidents.
Establish a Zero-Trust Policy
Establishing a Zero Trust policy is a cybersecurity approach that assumes no trust within or outside an organisation’s network. The solution requires continuous verification and strict access controls for all users and devices.
Implementing a Zero Trust model helps protect companies against insider threats as well as external attacks. The key to the strategy is to verify instructions or requests have come from the individual that is perceived to have sent the email or made a phone call.
One example doing the rounds tells the story of a CEO that went on holiday. A couple of days later a clerk in accounts received an email from the CEO telling her he had forgotten to pay an invoice. The email even mentioned how much he was enjoying the sunshine.
Not suspecting the email or the invoice would be fake the accounts clerk paid a good sum of money into the hacker’s bank account.
This is why zero trust should be ingrained as a best practice. It may feel tedious, and for most companies, it will be. But it’s better to be tedious than unemployed.
Develop a Cybersecurity Incident Response Plan
A comprehensive incident response plan should outline how employees will respond to a fraud incident. This includes communication strategies, legal considerations, and steps for minimising damage.
The easiest way to implement a cyberattack response plan is to establish an incident report team. This gives the employee the burden-free hassle of simply forwarding an email with suspicious activity or providing an overview of the suspected attack for further investigation.
You will, therefore, need to define incident categories and determine how employees should report suspicious activity. Potential cybersecurity incidents should be based on their severity and impact.
For example, a malware attack would be a simple standard practice whereas accusations of suspected insider threats are much more serious.
IT Support in London
As cybercrime continues to evolve, it’s understandable that C-suite executives, business owners and IT managers have growing concerns. With IT professionals already stretched, precious little time is available to consistently research, plan and manage cybersecurity details as well.
A manageable and cost-effective strategy is to outsource your cybersecurity to IT support professionals in London. We can help you to plan, manage, detect and consistently evolve your IT security defences.
Micro Pro has more than twenty years of experience serving high-value companies and C-suite executives in London. Our IT specialists are also strategists and think out-the-box when it comes to implementing cybersecurity measures.
If you’re concerned about your existing cybersecurity defences, get in touch with our IT team in London. We are more than happy to discuss your concerns, assess your current set up and identify effective solutions.


