Hacking News: Threat Actors Targeting Mac Users With ‘Atomic’ macOS Stealer Malware

Business Insider report that a cybercrime network is flogging the Atomic macOS stealer kit that targets Apple MacBook users. The Atomic Stealer malware (aka AMOS) is being offered to buyers for $1000/month in private chatrooms on Telegram.
Information-stealing malware is a troubling trend that can threaten the continuity of SMEs. Atomic macOS stealer malware can give hackers access to sensitive information, such as personal data, financial information, and intellectual property.
Because a data breach can lead to identity theft, financial fraud, and other damaging consequences, businesses are obligated to inform parties that have had sensitive data stolen and could be affected.
And the damage to your reputation can be devastating.
Surveys show that consumers lose faith in companies that suffer a data breach. According to TechWire Asia, 39% of consumers said they lost trust in a company that had been hacked.
Worse still, 88% of customers won’t use a brand they don’t think is capable of protecting their data. As more consumers become aware of data security issues, their trust in businesses is becoming increasingly “fragile”.
With hacking tools being sold on the dark web, the average hacker Joe can get their hands on effective malware to carry out illicit activities. And that potentially puts your business at risk.
What Is Atomic macOS Stealer Malware?
While Apple macOS users are not targeted as often as Microsoft users, this latest malware discovery underscores that nobody is safe. MacBooks are typically preferred by creatives and freelancers but are a popular choice in creative businesses as well.

Hackers look to install information-stealing malware on machines through various means. Malicious links in phishing emails in the primary modus operandi. Exploiting system vulnerabilities and man-in-the-middle attacks are also common strategies.
Threat actors have various methods they use to steal passwords and other sensitive data — more of which you can learn about in our article 10 Techniques Hackers Use To Crack Passwords.
The Atomic macOS Stealer malware hackers can steal sensitive information including auto-fills, keychain passwords, cookies, digital wallets, credit cards stored in browsers and cryptocurrencies.
Nefarious users deposit a dmg file containing 64-bit Go-based malware. The Atomic macOS stealer then compresses stolen data into a ZIP file and encodes it before transmitting the stolen data to a C&C server URL via communication:- hxxp[:]//amos-malware[.]ru/sendlog
Discovery of the Atomic macOS Stealer malware was uncovered by Cyble Research and Intelligence Labs (CRIL). A report released after the discovery stated that the malware is constantly being improved to make it more effective — and attractive to buyers.
Cybersecurity News report that threat actors continuously upgrade the malware. The additional “services” showcased in a Telegram post on April 25th informed customers the malware features a:
- Web panel for managing victims
- Meta mask brute-forcing
- Stealing seed
- Stealing private keys
- Crypto checker
- Dmg installer
There is good news, however. Like any other malware, Atomic macOS stealer cannot access files without permission. By updating your access permissions, you increase your ability to detect unusual activities that could be malicious attack.
How To Defend Yourself Against Atomic macOs Stealer Malware
There are many ways to protect your business network from a data breach. We also have effective strategies that meet your business requirements and your budgets. As we have documented before, cybersecurity solutions don’t have to be expensive.
We’re not going to go over the same ground here. The strategies below are specific to the Atomic macOS Stealer malware.
Only Download Apps With A Proven History
This goes without staying. Make it a company-wide policy not to download apps from untrusted sources.
However, apps in the Apple store that target business users can still be infected with malware. Lifehacker listed seven malicious apps found last year.
IT security chiefs will need to implement company-wide policies that either prevent employees from downloading apps or make them aware of the dangers.
Businesses that adopt a BYOD model are more vulnerable. A safe strategy is to only allow app downloads that have a long-standing proven history.
Whilst a ‘proven app strategy’ makes it difficult for new apps — which could be better — to get any visibility, SMEs have to protect their own interests first.

Install a reputable anti-virus software (in addition to Macs built-in AV tools)
Whilst Apple’s XProtect anti-malware tools do a pretty good job of identifying existing malware and preventing infections, native AV tools are not a standalone answer.
A number of reports have revealed that MacBooks can still be infected. Hackers are always evolving their technologies to end ways past anti-virus software. The safe option is to double up on your malware protection tools.
Create strong passwords using a personal cypher
Creating a strong password is advice that is repeated consistently over the years. But according to reports, weak passwords continue to invite bad actors onto business networks.
We recommend using a personal cypher. This can be as simple or as complicated as you like. The key is to create a passphrase that is personal to you but includes a sufficient level of complexity such as something random you might say to yourself.
You then type out the passphrase using the cypher.
For example, an A can be replaced with @, an S replaced with $ and an E with 3 etc. Your passphrase should also be something personal, albeit not related to information that might be known publicly such as the name of your pets, children or school nickname.
Here are some examples:
G00dVV1n3Gr3@tC0mp@ny – Good wine great company
R3@dy4@h0l1d@y – Ready for a holiday
Enable Biometric Security Features
Apple Macs give users the option to provide biometric data as an access security feature. To date, Touch ID and Face ID is limited to accessing a MacBook device. The next evolution will surely be to your biometric data as a multi-factor authentication strategy to access work apps that stores sensitive data.
Biometric security data provides a higher level of security than traditional password-based systems, which can be compromised through password guessing, social engineering, or other means.
Because biometric data, such as fingerprints, facial recognition, or iris scans are unique to each individual they cannot be easily replicated or shared by hackers.
Biometric security features also allow instant access rather than waiting for an MFA code to be sent via text message or email. Employees may be a little disconcerted by biometric app access at first but they will appreciate the convenience it offers over existing MFA strategies.
Plus they are already desensitised to biotic access on their phones and computers. It is less likely the resistance will be as fierce these days as it might have been a couple of years ago.
Scrutinise Emails
Data breaches can easily be diverted if your employees know where cybersecurity threats can come from. And more importantly, how to identify them when they drop into their inbox.
And phishing emails are being dropped all the time — every 11 seconds according to the internet.
The prevalence of phishing emails almost means it’s inevitable your employees will be attacked. Whilst some phishing emails are easy to spot — like the attempt below that was sent to one of our clients, flawlessly designed spoofing emails can escape attention.
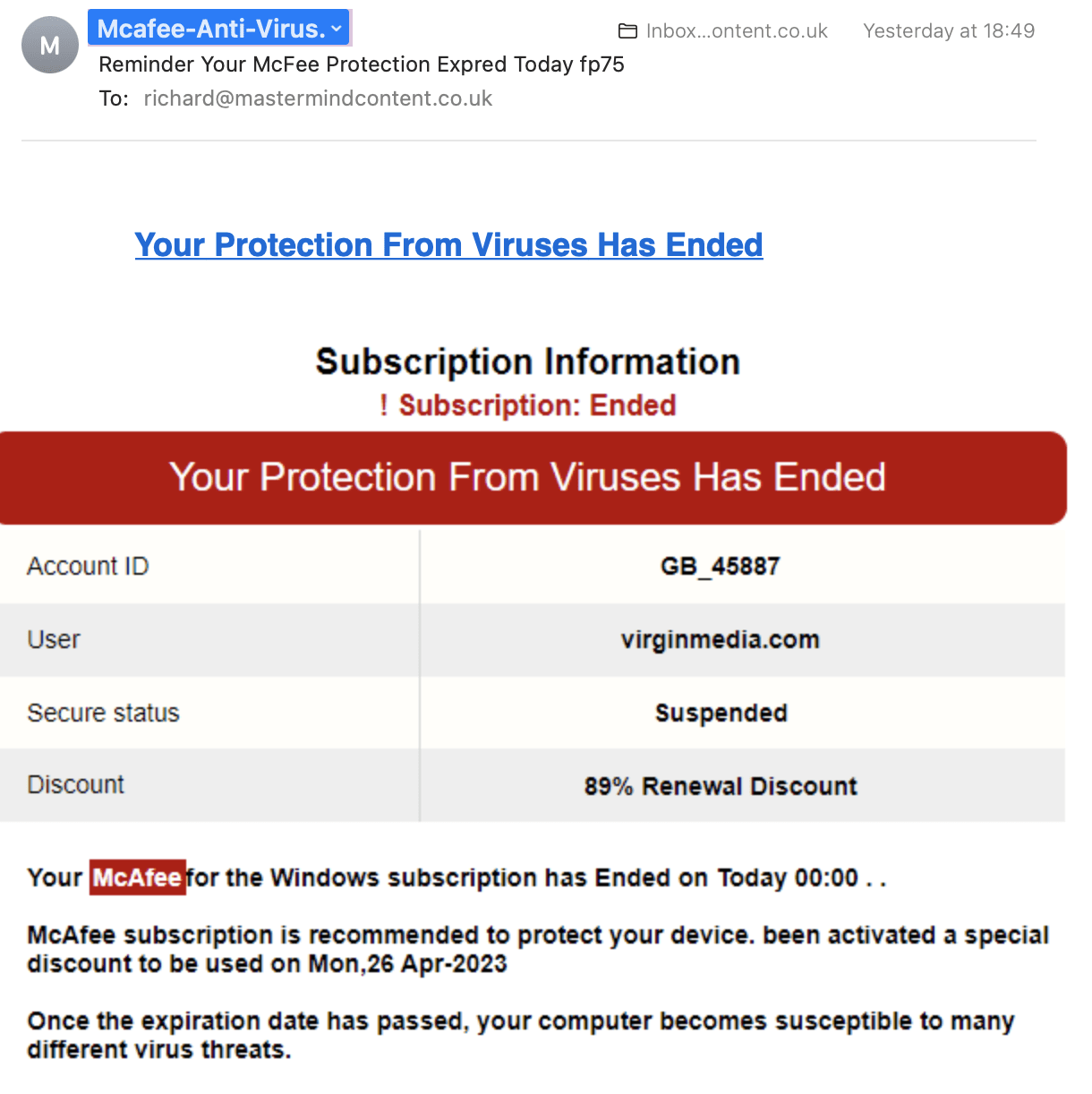
Instil strict protocols on your employees. Before clicking on links or opening documents sent by email, routinely perform the following checks. The email address from the sender was not McAfee, not does our client use McAfee.
But spoofing emails that appear to be from a company you are associated with, on the other hand, could trick employees into clicking links or attachments. That’s why Microsoft is so often used in spoof campaigns.
Here’s what to do when you get emails that could be potentially harmful.
Check the sender’s email address
Spoofing emails often have a sender’s email address that looks similar to a legitimate one but contains minor variations. Check the email address carefully and look for any discrepancies or inconsistencies.
Some examples:
Look for spelling and grammar errors
Spoofing emails from non-English speaking hackers often contain spelling and grammar errors. Or they are just badly worded. Also, any emails that open with ‘Dear customer’ are unlikely to be legitimate. If they’re not fraudulent, they’re spam.
Avoid clicking on links or downloading attachments
Illicit emails often contain links or attachments that can install malware or direct you to a phishing site. Avoid clicking on any links or downloading attachments unless you are absolutely certain that the email is legitimate.
Malicious links and attachments usually have hidden text so they cannot be detected by email filters. Hovering your mouse pointer over a link reveals a URL or file name. Malicious files have a suspicious link address.
Check for urgency or threats
Threat actors often contain urgent or threatening language that is designed to elicit a quick response from the recipient. Be wary of emails that demand immediate action or threaten negative consequences if you do not respond.
Check for unusual requests
Unusual requests such as asking you to provide sensitive information or transfer money should always be treated with suspicion. You can make these easier to spot by implementing systematic protocols — particularly for employees that might ordinarily receive such requests.
An effective strategy hackers use in spear phishing and whaling attacks is to pose as a trusted content. For example, a clerk in accounts might receive an email from the CEO asking them to pay an invoice — but the invoice is actually fake and includes an ‘unknown’ bank account.
Another tactic you should be wary of is an email from a supplier informing you they have changed their address. If their system has been hacked, it is possible for bad actors to use their email accounts to send fake invoices.
Update Software Promptly
Security updates are designed to fix security vulnerabilities that have been discovered in an operating system, application, or hardware that has been released onto the market by a software company.

Cybercriminals can exploit these vulnerabilities relatively easily — especially when they know where the vulnerability is. Software companies have to announce the security update and provide information about the potential gateway.
This inevitably gives cybercriminals a heads-up. Hackers that are good with code won’t have too much problem exploiting the vulnerability that has been left open by a business that has not performed a security update promptly.
Place Social Media Controls
Again, this comes back to raising cybersecurity awareness among your employees. Firms can’t prevent employees from using social media accounts, but you can inform your staff to limit the amount of personal information they share on social media platforms.
Hackers can use information extracted from social media networks to create personalised phishing emails — which can make spearphishing and whaling targets even more vulnerable.
For more information about how and who is the target of whaling and spearphishing attacks, check out our article, Are Hackers Targeting Your C-Suite With Whaling Attacks?
IT Security Solutions in London
Cybersecurity threats are not going away any time soon. It’s important to make sure you’re protecting — and equally important to keep up-to-date with the latest IT security risks.
For many UK companies, the best solution is to seek assistance and consult with experienced IT security professionals in London. When you have a team of experienced IT specialists watching over you, the risk of suffering a data breach is significantly lowered.
Teaming up with our cybersecurity experts protects your sensitive data from being stolen and ensures your employees are properly informed of potential threats.
Our customised IT packages include implementing an effective cybersecurity strategy, planning, ongoing management and proactive prevention together with providing continual awareness of the latest cybersecurity threats.
If you want to know more about how our team of specialists can help support your business, contact us today and speak to one of our knowledgeable experts.